Zero Trust Security
Introduction
Epitechnic’s Zero Trust Security Service is designed to enhance your organisation’s security posture by assessing, planning, and implementing a Zero Trust strategy tailored to your specific needs.
This comprehensive approach ensures that your security measures are robust, future-ready, and aligned with industry best practices.


Who should use this service?
This service is ideal for organisations at any stage of their Zero Trust journey, whether you are initiating your implementation or refining an existing strategy.
Service overview
Epitechnic’s Zero Trust Security Service offers a comprehensive approach to help organisations enhance their security posture by assessing, planning, and implementing a Zero Trust strategy.
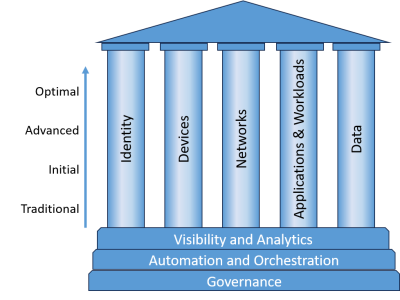
Designed to align with industry best practices, this service provides a structured framework to evaluate and advance your organisation’s maturity across the five Zero Trust pillars and three cross-cutting capabilities.
Business benefits
A Zero Trust strategy enables organisations to achieve a robust, adaptive security posture that supports innovation and growth, while safeguarding critical assets.
Future-ready architecture
Build a sustainable security model that supports digital transformation initiatives
Compliance alignment
Ensure adherence to applicable regulatory and industry standards
Enhanced security resilience
Strengthen your organisations defences against advanced threats and breaches
Tailored solutions
Receive bespoke recommendations designed to meet your specific needs and priorities
Improved governance
Establish clear processes for ongoing evaluation and accountability
Innovation and growth
Achieve a robust, adaptive security posture that supports innovation and growth, while safeguarding critical assets.
How we can help
Maturity assessment
We gain a clear understanding of your organisation’s current security posture through a comprehensive evaluation of existing practices.
Focus Areas:
Five Zero Trust Domains: Identity, Devices, Network, Applications and Workloads, Data.
Three Cross-Cutting Capabilities: Visibility and Analytics, Automation and Orchestration, Governance.
Key Business Benefits:
Identify vulnerabilities and gaps that could expose your business to risks.
Prioritise areas that need immediate attention to reduce the likelihood of breaches.
Empower stakeholders with actionable insights to drive informed decision-making.
Deliverable:
A business-focused visual report illustrating your Zero Trust maturity baseline, with clear recommendations for both tactical and strategic improvements.
Strategic planning
We will develop a customised Zero Trust roadmap to align your security strategy with your organization’s goals.
Key Business Benefits:
Align security investments with operational priorities and business objectives.
Minimise risks by addressing your organisations unique threat landscape and risk appetite.
Build a forward-looking security model that supports innovation and compliance needs.
Deliverable:
A detailed, actionable roadmap with prioritised initiatives and a clear timeline designed to meet operational goals, regulatory compliance requirements, and long-term business vision.
Implementation management
Drive the adoption and maturity of Zero Trust capabilities with expert guidance and seamless execution.
Key Business Benefits:
Ensure a smooth transition to Zero Trust with minimal disruption to operations.
Optimise existing security investments by integrating Zero Trust solutions into current architectures.
Measure progress effectively with defined metrics and KPIs to ensure continuous improvement.
How We Help:
Provide step-by-step guidance for implementing Zero Trust technologies.
Integrate solutions without disrupting day-to-day operations, ensuring business continuity.
Establish measurable KPIs to track and demonstrate ROI from your Zero Trust initiatives.
Why choose our Zero Trust Security Service?
-
Business-centric approach
Every step is designed to maximise the value of security investments while supporting your organisations growth.
-
Tailored solutions
We align our recommendations and implementations with your unique business goals and challenges
-
Future-ready security
We help you build a scalable and sustainable security framework that supports digital transformation and innovation.
