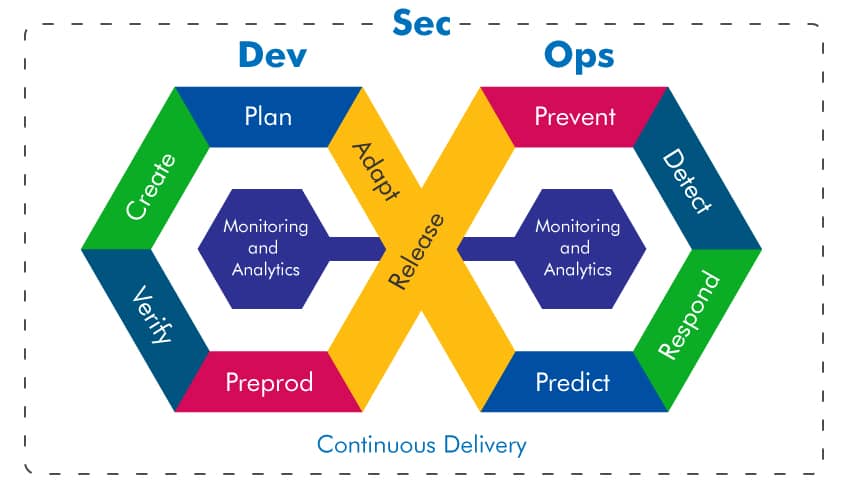
In recent years, the escalation of software supply chain attacks has underscored the critical vulnerabilities within the digital infrastructure of modern enterprises. The NIST SP 800-204D document emerges as a pivotal guide in this context, advocating for the integration of security measures into DevSecOps CI/CD pipelines to mitigate these risks. By embedding security at every stage of the software development lifecycle, organizations can significantly enhance their defenses against sophisticated cyber threats targeting the software supply chain.
 Among the notable attacks that have made headlines and underscored the urgency of adopting robust security practices include the SolarWinds attack in 2020, which saw malicious actors compromise the company’s management software, affecting thousands of businesses and government agencies. This incident not only demonstrated the far-reaching consequences of a single breach but also highlighted the sophistication of techniques employed by attackers. Similarly, the Dependency Confusion attack in 2021 exploited naming conventions in package management systems to breach high-profile targets such as Microsoft, Apple, and Tesla, showcasing the vulnerabilities inherent in open-source and third-party components.
Among the notable attacks that have made headlines and underscored the urgency of adopting robust security practices include the SolarWinds attack in 2020, which saw malicious actors compromise the company’s management software, affecting thousands of businesses and government agencies. This incident not only demonstrated the far-reaching consequences of a single breach but also highlighted the sophistication of techniques employed by attackers. Similarly, the Dependency Confusion attack in 2021 exploited naming conventions in package management systems to breach high-profile targets such as Microsoft, Apple, and Tesla, showcasing the vulnerabilities inherent in open-source and third-party components.
The SolarWinds attack in 2020 not only demonstrated the far-reaching consequences of a single breach but also highlighted the sophistication of techniques employed by attackers.
These incidents, along with others like the Mimecast certificate compromise in 2021 and the ASUS Live Update software backdoor in 2018, illustrate the diverse and evolving landscape of threats facing the software supply chain. They underscore the importance of NIST’s guidance for adopting a comprehensive and proactive approach to security, particularly in leveraging DevSecOps principles to ensure the integrity and resilience of software products. As organisations continue to grapple with these challenges, the lessons learned from past attacks and the strategies outlined in NIST SP 800-204D will be instrumental in shaping more secure software development and deployment practices for the future.
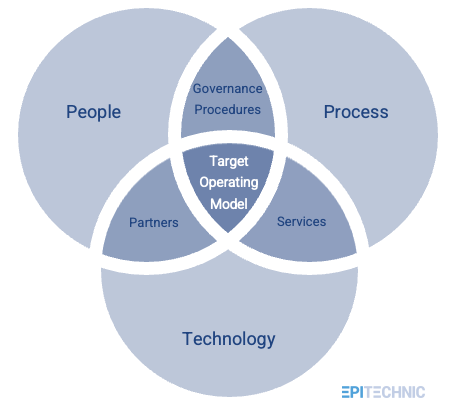
At the heart of the document lies a comprehensive framework designed to integrate security seamlessly into DevSecOps and CI/CD pipelines, addressing the multifaceted challenges of software supply chain security. The document lays out a series of best practices and recommendations that are pivotal for organisations aiming to safeguard their software development processes. Central to its guidance is the emphasis on the early integration of security measures, advocating for a ‘shift left’ approach where security considerations are embedded from the outset of the software development lifecycle. This includes rigorous vulnerability management, the use of automated tools for continuous security assessment, and the implementation of strong governance to oversee the entire supply chain.
The document lays out a series of best practices and recommendations that are pivotal for organizations aiming to safeguard their software development processes.
By delineating a structured approach to identifying, assessing, and mitigating risks, NIST SP 800-204D serves as an essential blueprint for organisations navigating the complexities of modern software development. It underscores the importance of transparency, accountability, and collaboration across all stakeholders involved in the software supply chain. Moreover, the document highlights the critical role of open-source software management, recommending practices for monitoring and securing open-source components which have become integral to software ecosystems.